First released in 2010, MediaGet has been around for a while. Initially, the torrent client was available in Russian only, but the team later expanded its reach across the world.
While it’s a relatively small player, it has been installed on millions of computers in recent years. It still has a significant reach, which is what Microsoft also found out recently.
This week the Windows Defender Research team reported that a poisoned version of the BitTorrent client was used to start the Dofoil campaign, which attempted to offload hundreds of thousands of malicious cryptocurrency miners.
Although Windows Defender caught and blocked the culprit within milliseconds, the team further researched the issue to find out how this could have happened.
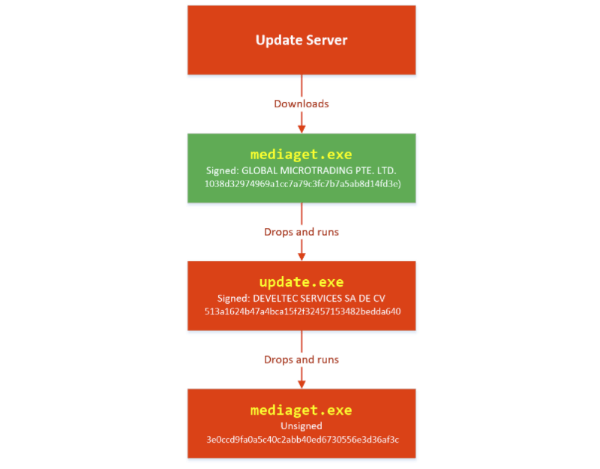
It turns out that the update process for the application was poisoned. This then enabled a signed version of MediaGet to drop off a compromised version, as can be seen in the diagram below.
“A signed mediaget.exe downloads an update.exe program and runs it on the machine to install a new mediaget.exe. The new mediaget.exe program has the same functionality as the original but with additional backdoor capability,” Microsoft’s team explains.
The malicious MediaGet version eventually triggered the mass coin miner outbreak. Windows Defender Research stresses that the poisoned version was signed by a third-party software company, not MediaGet itself.
Once the malware was launched the client built a list of command-and-control servers, using embedded NameCoin DNS servers and domains with the non-ICANN-sanctioned .bit TLD, making it harder to shut down.
More detailed information on the attack and how Dofoil was used to infect computers can be found in Microsoft’s full analysis.
MediaGet informs TorrentFreak that hackers compromised the update server to carry out their attack.
“Hackers got access to our update server, using an exploit in the Zabbix service and deeply integrated into our update mechanics. They modified the original version of Mediaget to add their functionality,” MediaGet reveals.
The company says that roughly five percent of all users were affected by the compromised update servers. All affected users were alerted and urged to update their software.
The issue is believed to be fully resolved at MediaGet’s end and they’re working with Microsoft to take care of any copies that may still be floating around in the wild.
“We patched everything and improved our verification system. To all the poisoned users we sent the message about an urgent update. Also, we are in contact with Microsoft, they will clean up all the poisoned versions,” MediaGet concludes.
 First released in 2010,
First released in 2010,