Well over three years have passed since Megaupload was shutdown, but there is still little progress in the criminal proceedings against the operation.
The United States hopes that New Zealand will extradite Kim Dotcom and his colleagues, but the hearings have been delayed several times already.
Meanwhile, several domain names including the popular Megaupload.com and Megavideo.com remain under the control of the U.S. Government. At least, that should be the case. In reality, however, they’re now being exploited by ‘cyber criminals.’
Instead of a banner announcing that the domains names have been seized as part of a criminal investigation they now direct people to a Zero-Click adverting feed. This feed often links to malware installers and other malicious ads.
One of the many malicious “ads” the Megaupload and Megavideo domain names are serving links to a fake BBC article, suggesting people can get an iPhone 6 for only £1.
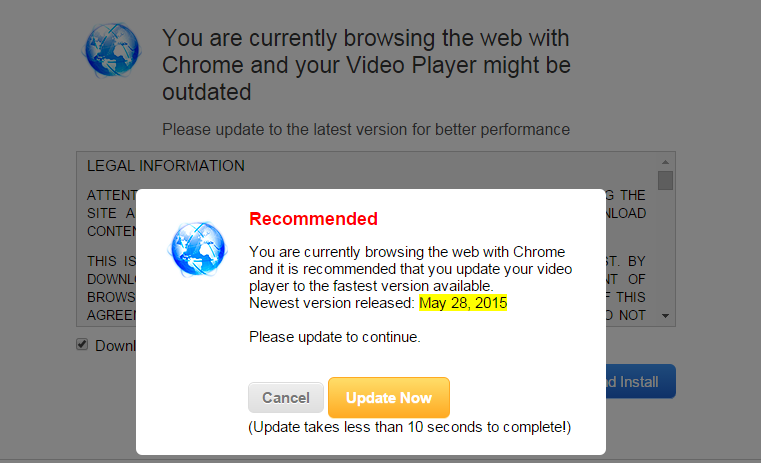
And here is another example of a malicious ad prompting visitors to update their browser.
The question that immediately comes to mind is this: How can it be that the Department of Justice is allowing the domains to be used for such nefarious purposes?
Looking at the Whois records everything seems to be in order. The domain name still lists Megaupload Limited as registrant, which is as it was before. Nothing out of the ordinary.
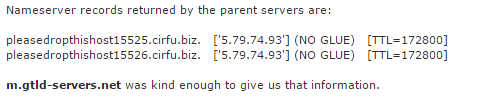
The nameserver PLEASEDROPTHISHOST15525.CIRFU.BIZ, on the other hand, triggers several alarm bells.
CIRFU refers to the FBI’s Cyber Initiative and Resource Fusion Unit, a specialized tech team tasked with handling online crime and scams. The unit used the CIRFU.NET domain name as nameserver for various seized domains, including the Mega ones.
Interestingly, the CIRFU.NET domain now lists “Syndk8 Media Limited” as registrant, which doesn’t appear to have any connections with the FBI. Similarly, CIRFU.BIZ is not an official CIRFU domain either and points to a server in the Netherlands hosted by LeaseWeb.
It appears that the domain which the Department of Justice (DoJ) used as nameserver is no longer in control of the Government. Perhaps it expired, or was taken over via other means.
As a result, Megaupload and Megavideo are now serving malicious ads, run by the third party that controls the nameserver.
This is quite a mistake for one of the country’s top cybercrime units, to say the least. It’s also one that affects tends of thousands of people, as the Megaupload.com domain remains frequently visited.
Commenting on the rogue domains, Megaupload founder Kim Dotcom notes that the people who are responsible should have known better.
“With U.S. Assistant Attorney Jay Prabhu the DOJ in Virginia employs a guy who doesn’t know the difference between civil & criminal law. And after this recent abuse of our seized Mega domains I wonder how this guy was appointed Chief of the Cybercrime Unit when he can’t even do the basics like safeguard the domains he has seized,” he tells TF.
“Jay Prabhu keeps embarrassing the U.S. government. I would send him back to law school and give him a crash course in ‘how the Internet works’,” Dotcom adds.
Making matters worse for the Government, Megaupload.com and Megavideo.com are not the only domain names affected. Various poker domains that were previously seized, including absolutepoker.com and ultimatebet.com, also link to malicious content now.
While the Government appears to have lost control of the old nameservers, it can still correct the problem through a nameserver update at their end. However, that doesn’t save those people who had their systems compromised during recent days, and it certainly won’t repair the PR damage.


 Well over three years have passed since Megaupload
Well over three years have passed since Megaupload